Getting Started with the Akamai Terraform Provider
Installing Terraform + CRUD Akamai configurations with Terraform
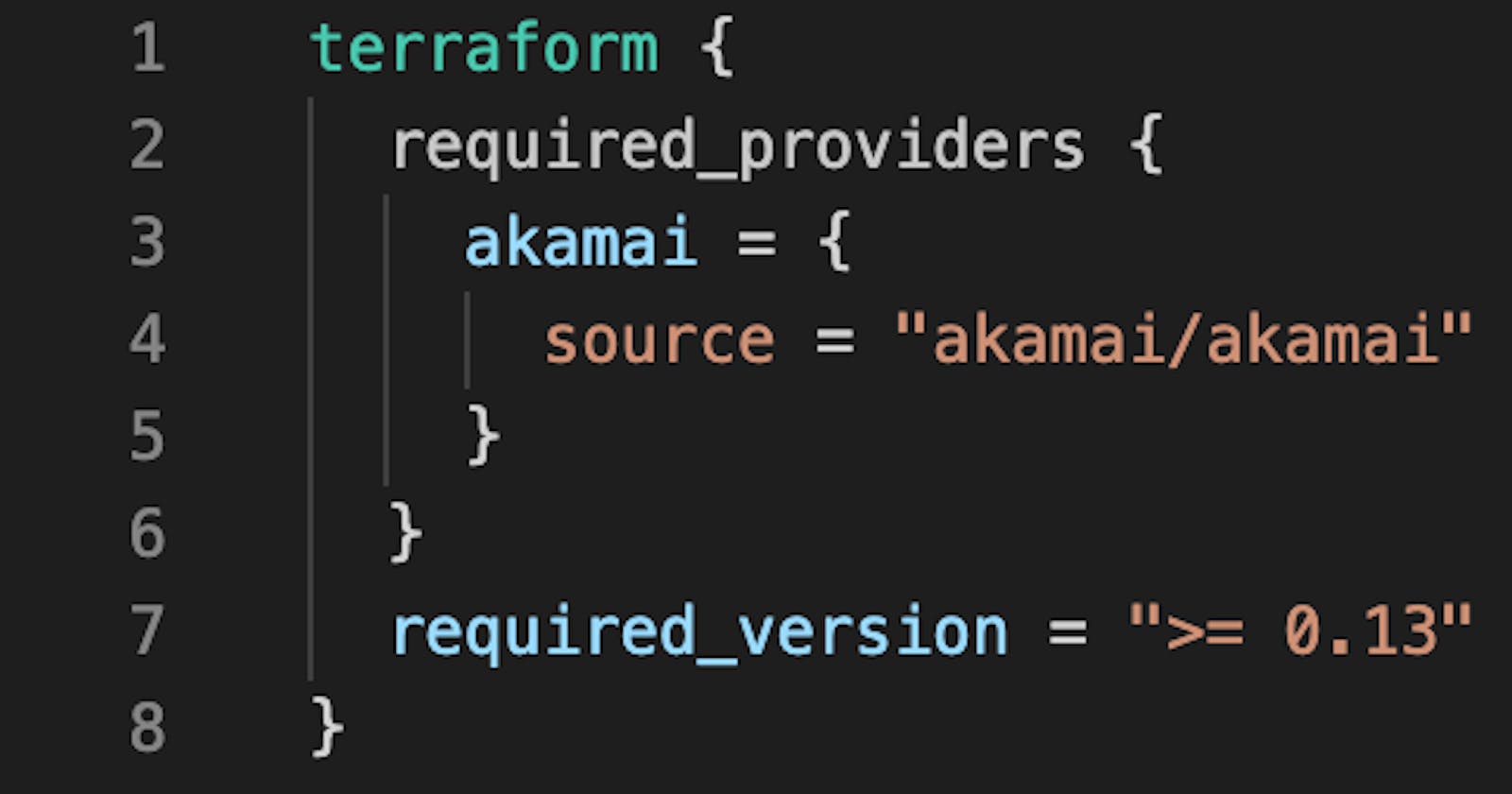
Akamai offers a HashiCorp Verified Terraform Provider to manage the solutions through Infrastructure as Code. The solutions include Content Delivery, Streaming Media, Web Application and API Protection, DNS and much more.
The documentation for the Akamai Terraform Provider can be found here:
Terraform Registry
The GitHub repository for the Akamai Terraform Provider can be found here: Akamai Terraform Provider on GitHub
In this article, you can find a Getting Started guide which aims at installing Terraform and creating your very first Akamai configuration.
This article is authored by Mike Elissen, Developer Advocate Akamai Developer and resident Terraform expert, in January 2022.
Why Terraform?
Terraform is currently the most popular Infrastructure as Code tool out there. Terraform is extremely helpful because it is vendor-agnostic and offers hundreds of unique Terraform Providers built by technology companies to manage their solutions through Infrastructure as Code.
With many companies adopting a DevOps / DevSecOps culture and automating as much as possible of their infrastructure, Terraform can be a very welcome asset as you only need to write HCL and have the ability to manage multiple vendors.
At Akamai, it is very common to have customers use Akamai to delivery and protect their web application and API endpoints, which are packaged in container platforms such as Docker and Kubernetes, which those are in turn hosted in the cloud with providers such as AWS, Google Cloud Platform and Microsoft Azure. They are also using platforms such as DataDog, ELK, Splunk etc. to ingest logs and monitor/observe their web applications and APIs. All of these technologies can be managed through the use of one tool - Terraform.
Terraform was released in 2014 and is managed by HashiCorp. The current release of Terraform is at version 1.1.3, is actively maintained and has millions of monthly users.
Installing Terraform
Terraform offers two ways to interface directly with it, the Terraform CLI or Terraform Cloud. This tutorial will be covering the Terraform CLI.
You can download the Terraform CLI here: Terraform Downloads
You can find instructions to complete the installation here: Terraform Install Instructions
As a MacOS user, I followed these steps to complete my installation:
- Download the MacOS Binary (AMD64 in my case)
- Unzip the binary and move the Terraform binary to my Downloads folder
- Start a Terminal session
- Run command 'echo $PATH' to verify where binaries are stored and executed. Output expected: /usr/local/bin:/usr/bin:/bin:/usr/sbin:/sbin:/usr/local/go/bin
- Run command 'mv ~/Downloads/terraform /usr/local/bin/' to move the Terraform binary from my Downloads folder to one of the $PATH folders. Please make sure you also have /usr/local/bin/ listed.
- Run command 'terraform --version' to make sure Terraform is working fine. Output expected: Terraform v1.1.3 on darwin_amd64.
Now you have Terraform CLI up and running. For instance run the command terraform --help for more information on the possible commands.
Terraform explained
Next we will need to create a Terraform configuration (.tf file) with our Terraform code. Terraform uses HCL, HashiCorp Configuration Language as the syntax. HCL, compared to other programming languages I have learned, is easy-to-read, simple-to-write.
Terraform configurations consist of two main concepts: data sources and resources.
A data source can typically be seen as 'reading information from outside', similar to a GET request when using APIs.. For instance, you would create a data source for the Akamai contract and group which retrieves the name and ID for these objects.
A resource is the most important Terraform concepts. A resource will be 'what creates the infrastructure', similar to a POST requests when using APIs. For instance, if you want to create an Akamai configuration, you would create a resource of the type 'akamai_property' with a unique name of your choosing.
When you run a terraform apply, the Terraform configuration gets parsed and each data source and resource gets processed, the output of which will be stored in a concept called the Terraform State file.
The Terraform workflow is quite simple. You write your Terraform configurations (or copy/paste templates) and run a simple three (or four) steps workflow:
- terraform init | Initialize terraform in your work directory, parse the .tf files and download any additional Terraform Providers you have declared.
- terraform plan | Parse your .tf files to have Terraform calculate what would happen if you apply this. This is a great way to make sure everything is good to go.
- terraform apply | Apply your resources and actually create or update the infrastructure you want with Terraform.
- terraform destroy | Optional, but terraform destroy will delete/remove/destroy any of your infrastructure if it is no longer required.
This should give a basic overview of Terraform. Before we fire up our favorite code editor (VS Code for me), let's go over Akamai terminology.
What is Akamai?
Akamai originated in the late 90s as one of the first Content Delivery Network vendors (CDN) and in the three decades has grown into one of the largest cybersecurity vendors available today.
Akamai offers the Akamai Intelligent Edge Platform to thousands of customers which has Akamai EdgeServers deployed in thousands of locations to be as close as possible to end-users accessing the Internet.
Akamai has a large portfolio of solutions available. In short, Akamai helps you deliver your web applications and API endpoints faster through performance optimizations techniques such as caching as well as protect them through the use of Web Application & API Protection, DDoS Protection (large volumetric attacks) and more. Akamai also offers way to deliver large software downloads and video content (live or on-demand) optimally to millions of users at once.
At Akamai, each customer entity has an Akamai contract with their solutions added on it. Each Akamai customer can also add Akamai users and groups to their account and manage the solutions through the use of the Akamai Control Center (control.akamai.com) . With the rise of Infrastructure as Code, Akamai started Akamai Developer as a way to offer other interfaces to manage Akamai, this includes Akamai API endpoints, an Akamai CLI as well as the Akamai Terraform Provider.
Akamai solutions are typically stored in an Akamai configuration where all of the features and settings are applied.
For instance:
- A web application or API endpoint is stored in an Akamai delivery configuration (property) with the hostname as the unique identifier. (securitylevelup.eu)
- All the application or API security settings are added to an Akamai security configuration (appsec) with the hostname again being the unique identifier.
- Additional concepts like an HTTPS Certificate, DNS records or even load-balancing, image optimization, Edge Computing functions and logging settings are managed with their own configurations/Terraform resources.
For each application or API endpoint, the DNS hostname will be routed and mapped to Akamai, which uses smart DNS mapping techniques to connect the end-user to the closest and best-performing Akamai EdgeServer.
Here is an example of an Akamai DNS CNAME chain:
www.securitylevelup.eu. 600 IN CNAME securitylevelup.akamaized.net.
securitylevelup.akamaized.net. 21600 IN CNAME a1625.dscr.akamai.net.
a1625.dscr.akamai.net. 20 IN A 23.217.99.187
My domain securitylevelup.eu is CNAMEd to Akamai (*.akamaized.net). The smart DNS mapping does it's magic and maps me to an Akamai EdgeServer located in Amsterdam, the Netherlands, where I am based.
When the Akamai EdgeServer 23.217.99.187 (or any of them of course) receives an HTTP(S) request for securitylevelup.eu, it finds the corresponding Akamai delivery configuration and security configuration and applies all the necessary features.
Is this a legitimate request or triggered as a malicious attack? In case of an attack, the request get denied/blocked from moving on and an error will be returned. If it is legitimate, it will retrieve the HTML, CSS, JS and where possible, retrieve it from cache instead of retrieving it all the way from a datacenter or cloud provider where the original file is stored.
Now that you understand Akamai better, let's dive deeper into the Akamai Terraform configuration that we will be using as an example.
Akamai configuration explained
You can find the Akamai Terraform templates on my GitHub: Akamai Terraform Templates
Download, copy and store each of the files listed here:
- property.tf | The complete Terraform configuration you need to create an Akamai delivery configuration with the akamai/akamai provider.
- property.auto.tfvars | The Terraform variable file where you can fill in your own hostname and Akamai settings.
- property-snippets/main.json | The JSON file with all the Akamai delivery behaviors and settings, based on best practices, using Akamai Ion as the delivery solution.
No changes have to be made to the property.tf or main.json. These are all good to go and all you need to do is modify the property.auto.tfvars and add your specific settings.
Inside the property.tf, you will find the following:
- Specifying that we need the akamai/akamai Provider and we will authenticate with our .edgerc file (more on that in the next section).
Specifying all the Terraform variables we need.
A data source for the Akamai contract/account we own and are allowed to use.
- A data source for the Akamai group where configurations are stored.
A data source for the Akamai Property Rules template where we bind the main.json to our new property.
A resource for the Akamai property, where the magic happens.
- A resource for an Akamai CP Code, this is used for monitoring and traffic reporting.
- A resource for an Akamai EdgeHostname, this is for mapping our own hostname to the Akamai through a DNS CNAME.
- A resource for a Property Activation, so that we not just create the configuration, but also activate and deploy it to either Akamai Staging or Akamai Production.
Akamai authentication explained
In order to properly authenticate your Terraform apply to Akamai, you will need to have a valid Akamai API client with credentials. This is called Akamai EdgeGrid.
To create an Akamai API client with credentials, you will need (admin) access to an Akamai account. Instructions can be found here: Akamai TechDocs
Your Akamai API credentials will consist of a host (where you can send requests to Akamai), a client-token, a client-secret and an access-token. We recommend you to store these four tokens in a file called .edgerc stored in your Home directory and add the [default] at the top of file.
With the authentication good to go, we are now finally ready to set-up our very first Akamai delivery configuration with Terraform.
Creating and deploying your first Akamai configuration with Terraform
You can find the Akamai Terraform templates on my GitHub: Akamai Terraform Templates
1) Download and store the files above in your working directory.
If you have git installed, run the following: git clone github.com/securitylevelup/akamai-terraform..
2) Open your favorite code editor and open the 'property.auto.tfvars' file.
3) Add the following variables:
contract_id = "" //your Akamai Contract ID group_name = "" //your Akamai Group Name product_id = "prd_Fresca" //Akamai Product ID, Akamai Ion = prd_Fresca hostname = "" //your hostname you want to Akamaize cpcode_name = "" //your CP Code name, best practice is to make it similar to your hostname edge_hostname = "" //your Akamai EdgeHostname ending in .edgesuite.net, .akamaized.net or .edgekey.net origin_hostname = "" //your Origin Hostname where Akamai will retrieve the content ip_behavior = "IPV6_COMPLIANCE" //IPV4+IPV6 enabled with IPV6_COMPLIANCE FLAG. rule_format = "v2020-11-02" //latest stable Property Rule Format cert_provisioning_type = "DEFAULT" //DEFAULT = Secure By Default, CPS_MANAGED = CPS managed certificates akamai_network = "" //Akamai Network, staging or production email = "" //your email address for notications
4) Save the file.
5) Start a Terminal session.
6) Make sure you are in the right working directory.
7) Run the command 'terraform init'. Output excepted: 'Terraform has been successfully initialized!' Terraform has now downloaded the Akamai Terraform Provider and is ready to execute.
8) Run the command 'terraform plan'. Output expected: 'Plan: 4 to add, 0 to change, 0 to destroy.'
9) Run the command 'terraform apply' and if there is no error, enter 'yes'.
Output expected: akamai_edge_hostname.edge_hostname: Creating... akamai_cp_code.cp_code: Creating... akamai_edge_hostname.edge_hostname: Creation complete after 3s [id=ehn_4934200] akamai_cp_code.cp_code: Creation complete after 6s [id=cpc_1281736] data.akamai_property_rules_template.rules: Reading... data.akamai_property_rules_template.rules: Read complete after 0s [id=da39a3ee5e6b4b0d3255bfef95601890afd80709] akamai_property.akamai_property: Creating... akamai_property.akamai_property: Still creating... [10s elapsed] ... akamai_property_activation.activation: Still creating... [2m30s elapsed] akamai_property_activation.activation: Creation complete after 2m32s [id=prp_768245:STAGING]
Apply complete! Resources: 4 added, 0 changed, 0 destroyed.
This process will take up to 2-3 minutes to complete on Akamai Staging. It will take around 7-10 minutes to complete on Akamai Production.
You now have a working and deployed delivery configuration on Akamai. Next steps will be to test your configuration as well as to set-up a DNS record to go-live with your hostname.
Updating your Akamai configuration with Terraform
If you want to update your Akamai configuration with Terraform now that you have your first version deployed and activated, all you need to do is make any changes to the Terraform resources or in this case, the main.json file.
When you write your code changes, save them and run another 'terraform apply' you will notice that Terraform will output something in the form of: 'Plan: 0 to add, 2 to change, 0 to destroy.'
This will run the updates and you do not have to worry about versioning. A new version of your Delivery configuration will be created and tracked by the Terraform State file.
Building out your Akamai configuration with more modules and features
From this point, you can continue with building out your Akamai configuration by adding more features or modules. For instance, you can now add the Akamai security configuration or additional modules such as Cloudlets or DataStream.
For more information on these modules, I recommend looking at the Terraform Registry: Terraform Registry
Deleting / Destroying your Akamai configuration with Terraform
If you no longer need your Akamai configuration, you can destroy with the 'terraform destroy' command.
In this case, it will deactivate the Akamai delivery configuration from Akamai Staging or Production.
Be careful when using terraform destroy and make certain you are indeed ready to delete it. The good thing about Terraform is, that even with a destroy, you should still have the Terraform configuration ready to go and run a terraform apply again to recreate your infrastructure on Akamai simply and fast!
What next?
Managing Akamai (as Code) with Terraform is easy to do and can be an efficient and fun way to use Akamai. If you have any questions on using the Akamai Terraform Provider, feel free to let me know in the comments below or reach out to me Mike Elissen, happy to help you on your Akamai Developer journey!
How To Akamai Terraform Provider on YouTube
I have also created a 45 minute video tutorial / webinar on the Akamai Terraform Provider which you can find on YouTube: YouTube Video
Useful Links
Terraform Registry Akamai Terraform Provider on GitHub [My Terraform Tapas video series] (youtube.com/watch?v=hX6BvfpdP-I&list=PL..)
If you have made it all the way to the end, I want to thank you for taking the time to look at this tutorial! /Mike