Your APIs are enabling Server-Side Request Forgery (SSRF) attacks
Learn what SSRF is, why it is dangerous and how to prevent it.
As a security consultant who has worked closely with developers in the boom of API microservices development, I've seen firsthand how APIs can inadvertently expose organizations to the risk of Server-Side Request Forgery (SSRF) attacks. These types of attacks can be difficult to detect and can have severe consequences, including data breaches, system compromise, and even financial loss.
In this article, we'll explore how APIs can be vulnerable to SSRF attacks, what the consequences of these attacks can be, and most importantly, what developers can do to prevent them. By the end of this article, you'll have a better understanding of the risks posed by SSRF attacks and the steps you can take to protect your organization's APIs from this threat.
Server-Side Request Forgery (SSRF) is a type of attack that exploits a vulnerability in a web application or API that allows an attacker to make unauthorized requests from the server to other internal or external systems.
In the context of microservices architecture, APIs act as the interface between different microservices. They receive requests from clients, which cannot be trusted by default, and forward them to the appropriate microservice. An SSRF attack on an API can lead to unauthorized access to sensitive data and resources in the microservices system.
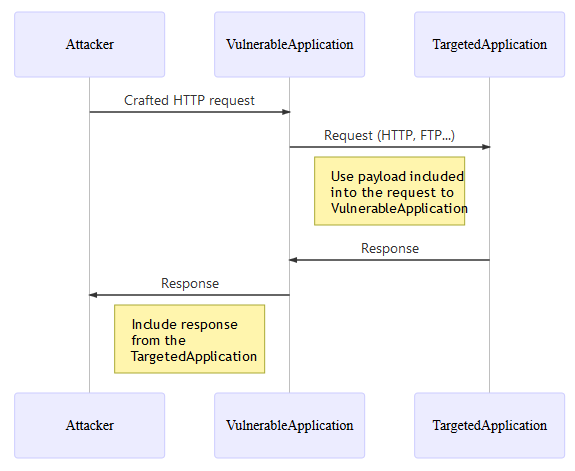
SSRF common attack flow, courtesy of OWASP
Here's how an SSRF attack on an API in a microservices architecture can work:
The attacker sends a request to the API with a specially crafted URL. The URL contains a parameter that specifies the target system the attacker wants to access.
The API receives the request and forwards it to the target system specified in the URL.
The target system responds to the request and sends the data back to the API.
The API returns the data to the attacker.
In this scenario, the attacker can use the API as a proxy to access other systems that may not be directly accessible to the attacker. For example, the attacker could use an SSRF attack to access a database that is only accessible from the internal network.
The consequences of an SSRF attack can be severe. Here are some anonymized examples of server-side request forgery (SSRF) attacks and the potential consequences they can have:
An attacker sends a malicious request to an e-commerce website's API microservices architecture, tricking it into fetching sensitive customer data from a third-party server. The attacker then uses this data to commit identity theft, causing reputational damage to the e-commerce website and resulting in potential revenue loss due to decreased customer trust.
An attacker exploits an SSRF vulnerability in a healthcare provider's API microservices architecture to access sensitive patient data. The attacker then sells this data on illegal marketplaces or applies extortion, causing significant reputational damage to the healthcare provider and potentially leading to legal action and financial penalties.
A financial institution's API microservices architecture is compromised by an attacker who uses SSRF to gain access to internal resources and transfer funds to a fraudulent account. This results in a significant financial loss for the institution and can damage its reputation, potentially leading to the loss of customers and revenue.
Overall, the consequences of an SSRF attack can be severe, ranging from reputational damage to financial loss and legal action. Organizations need to take steps to monitor and prevent SSRF attacks to protect their assets and maintain customer trust.
So how are attackers exploiting SSRF vulnerability in your API architecture? Here are some common examples of SSRF attacks:
Exploiting a vulnerable file upload feature: In this scenario, the attacker uploads a file with a specially crafted payload that tricks the server into making unauthorized requests to other internal or external systems.
Exploiting a misconfigured reverse proxy: In this scenario, the attacker sends a request to the web application that is then forwarded to a vulnerable reverse proxy. The attacker can then manipulate the request to make unauthorized requests to other systems.
Exploiting a vulnerable parameter: In this scenario, the attacker sends a request to the web application with a specially crafted parameter that causes the server to make unauthorized requests to other internal or external systems.
Exploiting an open redirect vulnerability: In this scenario, the attacker exploits an open redirect vulnerability in the web application to redirect the server to a malicious website, which then makes unauthorized requests to other systems.
Now that we understand how attackers are exploiting SSRF attacks and the consequences they can have. It is time to implement a strategy on how to monitor and prevent them.
Meet Aisha, who is a skilled developer and is always on the lookout for new threats to her company's API microservices architecture. One day, she learns about the dangers of Server-Side Request Forgery (SSRF) attacks, which can allow attackers to access unauthorized resources on her server. To protect her company's assets, Aisha prepares to battle against this potential threat using the following strategies:
The strategy of Input Validation: Aisha knows that the first line of defense against SSRF attacks is input validation. She ensures that all incoming requests are thoroughly checked for malicious input. She uses a variety of tools to validate the input, such as regex, type checking, and allowlist validation. Working with the front-end developers, they add these input validation checks in the latest development sprint.
The strategy of Access Controls: Aisha's second strategy is to implement access controls. She limits access to sensitive resources and blocks any unauthorized requests. She uses firewalls and access control lists to ensure that only authorized requests are allowed to pass through. Working with the security and network engineers, they utilize the concept of least privilege to lock down access inbound and outbound to API microservices and in between internal resources.
The strategy of Monitoring Network Traffic: Aisha's third strategy is to monitor network traffic for unusual requests. She uses various tools to monitor the network traffic, such as network analyzers and packet sniffers. She looks for unusual traffic patterns, such as a high volume of requests from a single IP address. Working with the Security Information and Event Management team, they add proper monitoring tools and processes on how to respond to threats clearly and concisely.
The strategy of Anomaly Detection: Aisha's fourth strategy is to implement anomaly detection. She creates a baseline of normal traffic patterns and uses machine learning algorithms to detect any deviations from this baseline. She also sets up alerts to notify her of any unusual activity together with the security researchers.
The strategy of Incident Response: Aisha's fifth strategy is to have an incident response plan in place. She creates a detailed plan that outlines what to do in case of a security incident. This includes steps such as isolating the affected system, notifying stakeholders, and gathering forensic evidence.
The strategy of Micro-Segmentation. Aisha's final strategy focuses on implementing micro-segmentation, more on this below.
By using these battle strategies, Aisha successfully defends her company's API microservices architecture from the threat of SSRF attacks. She knows that the battle is never truly won, as new threats will always emerge. But with a vigilant and proactive approach, she is confident that her company's assets are safe and secure.
The explanation above mirrors a real-world example in which I led the security consultancy of a media company that worked with Akamai to increase the security of their API microservices architecture by implementing a Web Application and API Protection (WAAP) solution offered as well as a micro-segmentation solution that can help with the prevention of security threats inside the network.
Micro-segmentation is a security technique that involves dividing a network into smaller, isolated segments, each with its security policies and controls. By using micro-segmentation to isolate resource fetching from API microservices to internal resources inside the network, organizations can limit the attack surface and reduce the risk of data breaches and other security incidents.
Here are some ways that micro-segmentation can help isolate resource fetching from API microservices:
Granular access control: Micro-segmentation allows organizations to define access controls at a granular level, which means that only authorized users or applications can access specific resources.
Segmentation of network traffic: By segmenting network traffic, organizations can ensure that only authorized users or applications can access specific resources, reducing the risk of unauthorized access or data breaches.
Network segmentation based on trust level: Micro-segmentation allows organizations to segment their network based on the trust level. This means that resources that require higher levels of trust can be placed in a separate segment with stricter access controls.
Automated network segmentation: Some micro-segmentation solutions use machine learning algorithms to automate the process of network segmentation, making it easier for organizations to manage their network security.
Zero-trust security model: Micro-segmentation aligns with the zero-trust security model, which assumes that no user or application is inherently trusted. Instead, all network traffic and user access requests are authenticated, authorized, and verified before access is granted.
By using micro-segmentation to isolate resource fetching from API microservices to internal resources inside the network, organizations can minimize the risk of attacks and unauthorized access, ensuring that their data and resources remain secure.
In conclusion, Server-Side Request Forgery (SSRF) attacks can have severe consequences, including reputational damage, financial loss, and legal action. As we have seen, APIs are particularly vulnerable to this type of attack, especially in API microservices architecture.
However, developers can take several steps to prevent SSRF attacks. The first step is input validation to ensure that all incoming requests are thoroughly checked for malicious input. The second step is access control to limit access to sensitive resources and block any unauthorized requests. The third step, monitoring network traffic for unusual requests can also be an effective strategy. And finally, by enabling micro-segmentation for the highest level of prevention.
By following these strategies, organizations and developers like Aisha can better protect their assets and maintain customer trust. Remember, prevention is always better than cure, so take action now to secure your API microservices architecture.
For more information on Server-Side Request Forgery and Akamai security solutions, here are helpful links:
Thanks for reading my article on server-side request forgery. SSRF is one of the more challenging security threats to tackle but one that should not be taken lightly. I hope my article has helped you level up your security knowledge and will enable you to protect your own API microservices architecture.
For any help with this, you can reach out to me in the comments on this blog or my LinkedIn.